AWS Serverless: Difference between revisions
Jump to navigation
Jump to search
| Line 27: | Line 27: | ||
</syntaxhighlight> | </syntaxhighlight> | ||
==Stack cowsay-lambda== | ==Stack cowsay-lambda== | ||
This stack or group of resources holds the lamda, bucket policy and role. The lambda function references the bucket created above | This stack or group of resources holds the lamda, bucket policy and role. The lambda function references the bucket created above.<br> | ||
[[File:Serverless framework.png |400px]] | [[File:Serverless framework.png |400px]] | ||
===IAM::Role=== | ===IAM::Role=== | ||
| Line 119: | Line 119: | ||
} | } | ||
</syntaxhighlight> | </syntaxhighlight> | ||
==Bucket Policy== | ==Bucket Policy== | ||
We need to allow lambda function access to the bucket. We do this with a the bucket | We need to allow lambda function access to the bucket. We do this with a the bucket | ||
Revision as of 02:41, 19 February 2022
Introduction
This is an example of how to set up a serverless framework function within AWS
Setup
Within AWS there are example templates for each piece of the infrastructure. For this we need to create a
- S3 Bucket to hold the code
- IAM::Role to describe the permissions
- Lambda The function to run
- Bucket Policy This grants access from the bucket to the lambda function
Templates
Here are the templates I used. I have highlighted where they differ from the provided examples
Stack cowsay-bucket
S3 Bucket
Example can be found here
This needs to be in its own stack and create prior to the other resources.
{
"Resources": {
"cowsayBucket": {
"Type": "AWS::S3::Bucket",
"Properties": {
"BucketName": "cowsayBucket"
}
}
}
}
Stack cowsay-lambda
This stack or group of resources holds the lamda, bucket policy and role. The lambda function references the bucket created above.
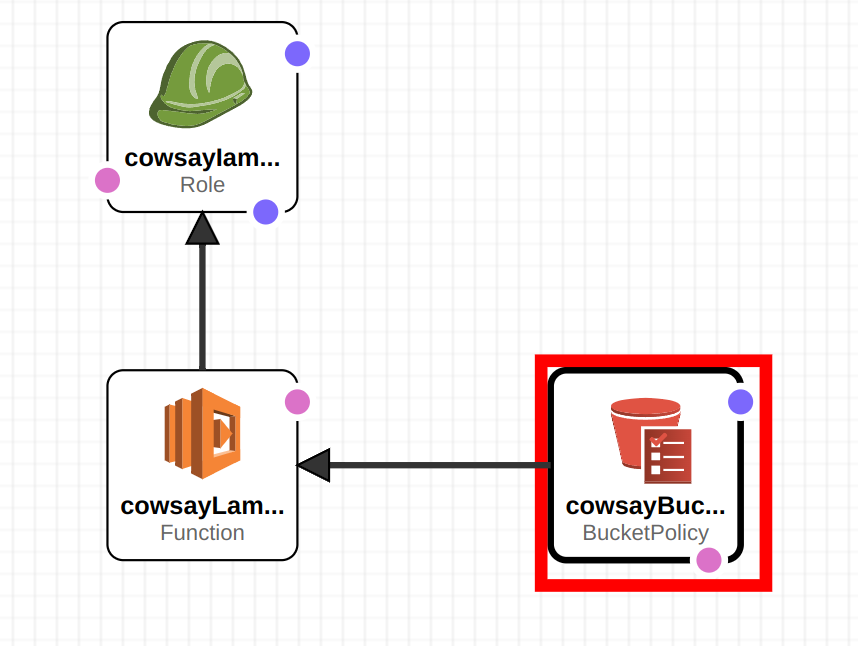
IAM::Role
Example can be found here
{
"Resources": {
"cowsayIamRole": {
"Type": "AWS::IAM::Role",
"Properties": {
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": [
"lambda.amazonaws.com"
]
},
"Action": [
"sts:AssumeRole"
]
}
]
},
"Path": "/",
"Policies": [
{
"PolicyName": "root",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:*"
],
"Resource": "arn:aws:logs:*:*:*"
}
]
}
}
]
}
}
}
}
Lambda Function
Example can be found here
{
"Resources": {
"cowsayLambda": {
"Type": "AWS::Lambda::Function",
"Properties": {
"Code": {
"S3Bucket": "cowsaybucket",
"S3Key": "cowsay.zip"
},
"Handler": "index.handler",
"Runtime": "nodejs14.x",
"Role": {
"Fn::GetAtt": [
"cowsayIamRole",
"Arn"
]
}
}
}
}
}
Adding the Role to the Lambda
Now we have the base templates we need to add properties to allow them to interact
{
"Resources": {
"cowsayBucket": {
"Type": "AWS::S3::Bucket",
"Properties": {
"BucketName": "cowsayBucket"
}
},
"Role": {
"Ref": "cowsayIamRole"
}
}
}
Bucket Policy
We need to allow lambda function access to the bucket. We do this with a the bucket
{
"Resources": {
"cowsayBucketPolicy": {
"Type": "AWS::S3::BucketPolicy",
"Properties": {
"Bucket": "cowsaybucket",
"PolicyDocument": {
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "serverlessrepo.amazonaws.com"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::cowsaybucket/*",
"Condition": {
"StringEquals": {
"aws:SourceArn": {
"Fn::GetAtt": [
"cowsayLambda",
"Arn"
]
}
}
}
}
]
}
}
}
}
}