Linux Setup
Pygmentize
So needed to update for keywords in C#. Here is the thrust of the changes based on. I used the code from https://github.com/FSund/pygments-custom-cpplexer
Python C# 9.0 Lexer
#!/usr/bin/python
from setuptools import setup, find_packages
setup(
name='pygments-mdcsharp90',
description='Pygments lexer for C# 9.0.',
long_description=open('README.md').read(),
keywords='pygments c# lexer',
packages=find_packages(),
install_requires=['pygments >= 1.4'],
entry_points='''[pygments.lexers]
mdcsharp90=pygments_mdcsharp90:MDCSharpLexer''',
classifiers=[
'Development Status :: 4 - Beta',
'Environment :: Plugins',
'Operating System :: OS Independent',
'Programming Language :: Python',
'Programming Language :: Python :: 2',
'Programming Language :: Python :: 3',
'Topic :: Software Development :: Libraries :: Python Modules',
],
)
#from pygments.lexers.asm import CppLexer
from pygments.lexers import CSharpLexer
from pygments.token import Name, Keyword
class MDCSharpLexer(CSharpLexer):
name = 'MDCSharp90'
aliases = ['mdcsharp90']
EXTRA_KEYWORDS = ['record', 'init']
def get_tokens_unprocessed(self, text):
for index, token, value in CSharpLexer.get_tokens_unprocessed(self, text):
if token is Name and value in self.EXTRA_KEYWORDS:
yield index, Keyword, value
else:
yield index, token, value
Fix BCM BCM43142A0 (0a5c:216)
Well this was a tougher than expected but not too tough for me.
First I tried to use the drivers on https://github.com/winterheart/broadcom-bt-firmware
Instructions were
- get the appropriate hid file and reboot
- copy to /lib/firmware
- reboot
- Look for Bluetooth. This is what bad looks light
Mar 17 01:15:20 BILL kernel: [ 2205.631184] Bluetooth: hci0: BCM: chip id 70
Mar 17 01:15:20 BILL kernel: [ 2205.632142] Bluetooth: hci0: BCM: features 0x06
Mar 17 01:15:20 BILL kernel: [ 2205.648147] Bluetooth: hci0: BILL
Mar 17 01:15:20 BILL kernel: [ 2205.648155] Bluetooth: hci0: BCM43142A0 (001.001.011) build 0000
Mar 17 01:15:20 BILL kernel: [ 2205.649174] Bluetooth: hci0: BCM: firmware Patch file not found, tried:
Mar 17 01:15:20 BILL kernel: [ 2205.649180] Bluetooth: hci0: BCM: 'brcm/BCM43142A0-0a5c-216c.hcd'
Mar 17 01:15:20 BILL kernel: [ 2205.649183] Bluetooth: hci0: BCM: 'brcm/BCM-0a5c-216c.hcd'
Mar 17 01:15:22 BILL kernel: [ 2207.661039] Bluetooth: hci0: command 0x1003 tx timeout
Mar 17 01:15:22 BILL kernel: [ 2207.662104] Bluetooth: hci0: unexpected event for opcode 0x1003
Mar 17 01:16:01 BILL kernel: [ 2246.952482] Bluetooth: hci0: urb 0000000034f8d926 failed to resubmit (2)
Mar 17 01:16:01 BILL kernel: [ 2246.952491] Bluetooth: hci0: urb 00000000f20ac1f5 failed to resubmit (2)Well let's pretend the sun went down, came up and went down again as I googled my way to getting this working. Knowing what good looks like is the key. I did not
So originally thought the site had taken hex files found in the drivers and converted them to hid. They may well have done but it did not work. So once I found this was what bad looks like this is what I did
- Found the drivers on line bluetooth_Win7-8-8-1_V6515800_12009860.zip
- Unzip and look for PID_216C (the id of the card)
- This will give a list on files. Look for the most sensible, my case (Win64) was Bluetooth_Win7-8-8-1_V6515800_12009860/Win8_Win81/Win64/bcbtums-win8x64-brcm.inf
- Look for the right hex file by again search for the PID
- In the section ;;;;;;;;;;;;;RAMUSB216C;;;;;;;;;;;;;;;;; only one hex file is listed
- This is BCM43142A0_001.001.011.0197.0233.hex
- Convert to hid file with hex2hcd BCM43142A0_001.001.011.0197.0233.hex -o BCM43142A0-0a5c-216c.hcd
- Copy file to /lib/firmware/brcm
- Reboot and cross fingers
- Attempt at own risk and I believe it is also illegal to dont do it
This is what good looks like
Mar 17 01:24:10 BILL kernel: [ 24.611457] Bluetooth: Core ver 2.22
Mar 17 01:24:10 BILL kernel: [ 24.611489] Bluetooth: HCI device and connection manager initialized
Mar 17 01:24:10 BILL kernel: [ 24.611493] Bluetooth: HCI socket layer initialized
Mar 17 01:24:10 BILL kernel: [ 24.611495] Bluetooth: L2CAP socket layer initialized
Mar 17 01:24:10 BILL kernel: [ 24.611499] Bluetooth: SCO socket layer initialized
Mar 17 01:24:10 BILL kernel: [ 25.253630] Bluetooth: hci0: BCM: chip id 70
Mar 17 01:24:10 BILL kernel: [ 25.254629] Bluetooth: hci0: BCM: features 0x06
Mar 17 01:24:10 BILL kernel: [ 25.270595] Bluetooth: hci0: BILL
Mar 17 01:24:10 BILL kernel: [ 25.270599] Bluetooth: hci0: BCM43142A0 (001.001.011) build 0233
Mar 17 01:24:10 BILL kernel: [ 25.508569] Bluetooth: hci0: BCM43142A0 'brcm/BCM43142A0-0a5c-216c.hcd' Patch
Mar 17 01:24:10 BILL kernel: [ 26.108639] Bluetooth: hci0: Broadcom 43142 Bluetooth 4.0 Adapter
Mar 17 01:24:10 BILL kernel: [ 26.108643] Bluetooth: hci0: BCM43142A0 (001.001.011) build 0233
Mar 17 01:24:13 BILL systemd[1]: Started Bluetooth service.
Mar 17 01:24:13 BILL systemd[1]: Reached target Bluetooth.
Mar 17 01:24:13 BILL kernel: [ 39.740491] Bluetooth: BNEP (Ethernet Emulation) ver 1.3
Mar 17 01:24:13 BILL kernel: [ 39.740493] Bluetooth: BNEP filters: protocol multicast
Mar 17 01:24:13 BILL kernel: [ 39.740499] Bluetooth: BNEP socket layer initialized
Mar 17 01:24:13 BILL bluetoothd[699]: Bluetooth management interface 1.17 initializedSnap
Onliners for me
snap list
snap refresh --list
snap refresh
Zoom
You need to download the zoom.deb from the site
apt install libgl1-mesa-glx libegl1-mesa libxcb-xtest0 libxcb-xinerama0
sudo apt install gdebi
sudo dpkg i ~/Download/zoom.deb
Making fakecam work
2022 Feb 28 - Could not get this to work with out turning off the apparmor for fakecam. Then you need to
sudo aa-complain snap.fakecam.fakecam -d /var/lib/snapd/apparmor/profile
sudo snap connect fakecam:camera
sudo fakecam
Gimp
Install flatpak
To install gimp we need to install flatPak. We can to this with
sudo apt install flatpak
Add Repositories
We then add the repositories. We need the beta for Gimp and the normal one for dependencies
flatpak remote-add --user flathub-beta https://flathub.org/beta-repo/flathub-beta.flatpakrepo
flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
# List repositories with
flatpak remote-list
Install Software
At the time I needed org.gnome.Platform//3.38. To find out which you can install in reverse. i.e.
flatpak install --user flathub-beta org.gimp.GIMP
Then install the software
# From flathub
flatpak install flathub org.gnome.Platform//3.28
# From flathub-beta
flatpak install --user flathub-beta org.gimp.GIMP
Network Stuff
ip link list eno1
ip link set eno1 down
ip link set eno1 up
netplan apply
Set up Monitors
Xorg.conf
This is in /etc/X11/xorg.conf
# nvidia-settings: X configuration file generated by nvidia-settings
# nvidia-settings: version 465.31
Section "ServerLayout"
Identifier "Layout0"
Screen 0 "Screen0" 0 0
InputDevice "Keyboard0" "CoreKeyboard"
InputDevice "Mouse0" "CorePointer"
Option "Xinerama" "0"
EndSection
Section "Files"
EndSection
Section "InputDevice"
# generated from default
Identifier "Mouse0"
Driver "mouse"
Option "Protocol" "auto"
Option "Device" "/dev/psaux"
Option "Emulate3Buttons" "no"
Option "ZAxisMapping" "4 5"
EndSection
Section "InputDevice"
# generated from default
Identifier "Keyboard0"
Driver "kbd"
EndSection
Section "Monitor"
# HorizSync source: edid, VertRefresh source: edid
Identifier "Monitor0"
VendorName "Unknown"
ModelName "AOC V27t"
HorizSync 30.0 - 80.0
VertRefresh 55.0 - 75.0
Option "DPMS"
EndSection
Section "Device"
Identifier "Device0"
Driver "nvidia"
VendorName "NVIDIA Corporation"
BoardName "NVIDIA GeForce GT 1030"
EndSection
Section "Screen"
# Removed Option "metamodes" "HDMI-0: nvidia-auto-select +939+0, DVI-D-0: nvidia-auto-select +0+0 {rotation=left}"
# Removed Option "metamodes" "nvidia-auto-select +0+0"
# Removed Option "metamodes" "1920x1080_60 +0+0"
# Removed Option "metamodes" "HDMI-0: nvidia-auto-select +0+0 {AllowGSYNC=Off}, DVI-D-0: nvidia-auto-select +1920+0 {AllowGSYNC=Off}"
# Removed Option "metamodes" "HDMI-0: nvidia-auto-select +1200+546 {AllowGSYNC=Off}, DVI-D-0: 1920x1200_60 +0+0 {rotation=left, AllowGSYNC=Off}"
Identifier "Screen0"
Device "Device0"
Monitor "Monitor0"
DefaultDepth 24
Option "Stereo" "0"
Option "nvidiaXineramaInfoOrder" "DFP-1"
Option "metamodes" "HDMI-0: 1920x1080 +1200+546 {AllowGSYNC=Off}, DVI-D-0: 1920x1200_60 +0+0 {rotation=left, AllowGSYNC=Off}"
Option "SLI" "Off"
Option "MultiGPU" "Off"
Option "BaseMosaic" "off"
SubSection "Display"
Depth 24
EndSubSection
EndSectionXrand
Screen 0: minimum 8 x 8, current 3840 x 1200, maximum 32767 x 32767
DVI-D-0 connected 1920x1200+1920+0 (normal left inverted right x axis y axis) 518mm x 324mm
1920x1200 59.95*+
1920x1080 60.00
1680x1050 59.95
1600x1200 60.00
1280x1024 60.02
1280x960 60.00
1024x768 60.00
800x600 60.32
640x480 59.94
HDMI-0 connected primary 1920x1080+0+0 (normal left inverted right x axis y axis) 598mm x 340mm
1920x1080 60.00*+ 59.94 50.00 60.00 50.04
1680x1050 59.95
1440x900 59.89
1280x1024 75.02 60.02
1280x960 60.00
1280x720 60.00 59.94 50.00
1024x768 75.03 60.00
800x600 75.00 60.32
720x576 50.00
720x480 59.94
640x480 75.00 59.94 59.93Monitors.xml
Change .config/monitor.xml, test and copy to
sudo cp ~/.config/monitors.xml /var/lib/gdm3/.config/
sudo chown gdm:gdm /var/lib/gdm3/.config/monitors.xml
My monitor 2020-09-07
<monitors version="2">
<configuration>
<logicalmonitor>
<x>0</x>
<y>0</y>
<scale>1</scale>
<transform>
<rotation>left</rotation>
<flipped>no</flipped>
</transform>
<monitor>
<monitorspec>
<connector>DVI-D-0</connector>
<vendor>DEL</vendor>
<product>DELL U2412M</product>
<serial>9W5YH33E2ECS</serial>
</monitorspec>
<mode>
<width>1920</width>
<height>1200</height>
<rate>59.950172424316406</rate>
</mode>
</monitor>
</logicalmonitor>
<logicalmonitor>
<x>2400</x>
<y>0</y>
<scale>1.25</scale>
<primary>yes</primary>
<monitor>
<monitorspec>
<connector>HDMI-0</connector>
<vendor>AOC</vendor>
<product>V27t</product>
<serial>0x01010101</serial>
</monitorspec>
<mode>
<width>1920</width>
<height>1080</height>
<rate>60</rate>
</mode>
</monitor>
</logicalmonitor>
</configuration>
</monitors>
Set up Apache HSTS
In Apache 2 000-default.conf
<VirtualHost *:80>
ServerName example.com
Redirect permanent / https://example.com/
</VirtualHost>
In Apache 2 default-ssl.conf
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains;"
On time setups on 19.04 upwards
To add scaling
gsettings set org.gnome.mutter experimental-features "['x11-randr-fractional-scaling']"
Auto hide taskbar
Go to settings->dock->auto-hide the dock
Hide top bar
sudo apt install gnome-shell-extension-autohidetopbar
- log out
- log in
- run gnome-tweak
- extension->Hide to bar
On time setups on 20.04 upwards
Mediwiki
Create database
CREATE DATABASE my_wiki
CREATE USER 'newuser'@'localhost' IDENTIFIED BY 'password';
GRANT ALL PRIVILEGES ON * . * TO 'newuser'@'localhost';
Restore database
mysql -u root -p XXXX < db_backup_XXXX_23_10_2019_04_21_44
Copy Wiki files
cp <backup>/mediawiki /var/lib/mediawiki
Postfix
Good Site for Spam Protection
Found this site useful https://www.linuxbabe.com/mail-server/block-email-spam-postfix
>br>
Current main.cf
...
smtpd_helo_required = yes
smtpd_helo_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_invalid_helo_hostname
reject_non_fqdn_helo_hostname
reject_unknown_helo_hostname
smtpd_sender_restrictions =
permit_mynetworks
permit_sasl_authenticated
reject_unknown_sender_domain
reject_unknown_reverse_client_hostname
reject_unknown_client_hostname
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated
check_policy_service inet:127.0.0.1:10023,
check_client_access hash:/etc/postfix/rbl_override,
reject_rhsbl_helo dbl.spamhaus.org,
reject_rhsbl_reverse_client dbl.spamhaus.org,
reject_rhsbl_sender dbl.spamhaus.org,
permit_dnswl_client list.dnswl.org=127.0.[0..255].[1..3],
reject_rbl_client zen.spamhaus.org
...Create database
CREATE DATABASE mail
CREATE USER 'newuser'@'localhost' IDENTIFIED BY 'password';
GRANT ALL PRIVILEGES ON mail.* TO 'newuser'@'localhost' WITH GRANT OPTION;
mysql -u root -p XXXX < db_backup_my_XXXX_23_10_2019_04_21_44
Setup mail user and directory
cd /var
ln -s /mnt/<RAID ARRAY>/vmail .
groupadd -g 5000 vmail
useradd -m -d /var/vmail -s /bin/false -u 5000 -g vmail vmail
Setup Cetificates for SSL
systemctl stop apache2
apt-get install python3-certbot-apache
certbot -n --agree-tos --standalone certonly -d www.bibble.co.nz
certbot -n --agree-tos --standalone certonly -d mail.bibble.co.nz
certbot -n --agree-tos --standalone certonly -d imap.bibble.co.nz
Install postfix
apt-get install postfix
apt-get install postfix-mysql
apt-get install postfix-policyd-spf-python
apt-get install postgrey
apt-get install sasl2-bin libsasl2.2 libsasl2-modules
Install opendkim
apt-get install opendkim
cp -r /backup/etc/opendkim /etc
# Change /etc/opendkim.conf
Socket local:/var/spool/postfix/opendkim/opendkim.sock
# Change /etc/default/opendkim
Socket local:/var/spool/postfix/opendkim/opendkim.sock
# Change /etc/postfix/main.cf
smtpd_milters = local:opendkim/opendkim.sock
Install Amavisd And Spamassasin
apt-get install amavisd-new spamassassin \
clamav clamav-daemon unzip bzip2 libnet-ph-perl \
libnet-snpp-perl libnet-telnet-perl nomarch lzop
In /etc/amavis/conf.d/15-content_filter_mode uncomment
@bypass_virus_checks_maps = (
\%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re);Add to postfix
postconf -e 'content_filter = amavis:[127.0.0.1]:10024'
postconf -e 'receive_override_options = no_address_mappings'
systemctl restart amavis
systemctl restart clamav-daemon
systemctl restart postfix
usermod -a -G clamav amavis
usermod -a -G amavis clamav
Change /etc/amavis/conf.d/05-node_id to have
05-node_id:$myhostname = "denise.bibble.
Dovecot
apt install dovecot-imapd dovecot-pop3d apt install dovecot-sieve dovecot-solr dovecot-antispam apt-get install dovecot-mysql apt-get install dovecot-lmtpd
Setting netplan to render through network manager
network:
version: 2
renderer: NetworkManager
ethernets:
enp4s0:
addresses: [10.1.1.70/24]
gateway4: 10.1.1.99
nameservers:
search: [bibble.local]
addresses: [10.10.1.2]
dhcp4: noSetting up repo for current packages on ubuntu
Get list of package installd
$ apt list --installed > install.list
Then translate it into apt understandable format:
$ sed -r 's/ \[.*?\]//g' install.list | sed -r 's/(^.*?)\/.*?[ ](.*?)[ ](.*?)$/\1:\3=\2/g' > install.list.to.dl
Then download the current packages versions:
$ xargs apt download < install.list.to.dl
You would need to create a Packages.gz file in order to add this folder as a source for apt. E.g.
$ cd ~/deb_server/debs/ $ dpkg-scanpackages -m . /dev/null | gzip -9c > Packages.gz
EDIT: path for dpkg-scanpackages must be relative, otherwise this will break the download process later (-m allows you to have multiple versions, if you want the most recent version, remove the -m) Now you have to bring up a file server for example apache2 and configure it to index files.
/etc/apache2/sites-enabled/000-debserver.conf
Containing:
DocumentRoot /var/www
<Directory /var/www/>
Options +Indexes +FollowSymLinks
Require all granted
</Directory>
And finally you need to symlink the deb folder to /var/www. (Or configure the server to the current deb download location) e.g.
$ ln -s ~/deb_server/debs/ /var/www/repo
The last bit is to add the server machine as the only source for apt updates on each target machine.
$ deb [trusted=yes] http://deb_server_ip/repo /
If you want to update the packages, you need to re-run apt download of the list, but without the version.
$ sed -r 's/ \[.*?\]//g' install.list | sed -r 's/(^.*?)\/.*?[ ](.*?)[ ](.*?)$/\1:\3/g' > install.list.for.update $ apt update && xargs apt download < install.list.for.update
Setting up Iot Edge on 19.04
Not yet released so here is how to do it
Install docker
wget https://packages.microsoft.com/ubuntu/18.04/multiarch/prod/pool/main/i/iotedge/iotedge_1.0.8-2_amd64.deb wget https://packages.microsoft.com/ubuntu/18.04/multiarch/prod/pool/main/libi/libiothsm-std/libiothsm-std_1.0.8-1_amd64.deb wget http://archive.ubuntu.com/ubuntu/pool/main/o/openssl1.0/libssl1.0.0_1.0.2n-1ubuntu5.3_amd64.deb
Fixing ubuntu 19.04 mouse
Install kernel 5.2.x
Cerificates
Expiry Dates
You can see the expiry dates with certbot
certbot certificates
// Gives
Certificate Name: xxx.bibble.co.nz
Serial Number: xxxxxx
Domains: xxx.bibble.co.nz
Expiry Date: 2021-10-03 01:02:21+00:00 (VALID: 89 days)
Certificate Path: /etc/letsencrypt/live/xxx.bibble.co.nz/fullchain.pem
Private Key Path: /etc/letsencrypt/live/xxx.bibble.co.nz/privkey.pem
Initial
apt-get install software-properties-common python-software-properties
add-apt-repository ppa:certbot/certbot
apt-get update
apt-get install python-certbot-apache
certbot -n --agree-tos --standalone certonly -d <site1.domain.com>
certbot -n --agree-tos --standalone certonly -d <site2.domain.com>
Renew
sudo certbot -n --agree-tos --standalone certonly -d <site1.domain.com>
sudo systemctl restart dovecot
sudo systemctl restart nginx
sudo microk8 stop
sudo microk8 start
Building r8168
This is not necessary as you can use the command
apt-get install r8168-dkms
Updating DNS
This script runs in crontab once every 15 minutes
#!/bin/bash lynx -source -auth=user_xxx:pass_xxxx 'http://dynamic.zoneedit.com/auth/dynamic.html?host=bibble.co.nz' lynx -source -auth=user_xxx:pass_xxxx 'http://dynamic.zoneedit.com/auth/dynamic.html?host=denise.bibble.co.nz' lynx -source -auth=user_xxx:pass_xxxx 'http://dynamic.zoneedit.com/auth/dynamic.html?host=www.bibble.co.nz' lynx -source -auth=user_xxx:pass_xxxx 'http://dynamic.zoneedit.com/auth/dynamic.html?host=sync.bibble.co.nz'
Backup MySQL
I use the following script to back up the databases
#!/bin/sh
myBackupFolder="/home/iwiseman/backups"
myBackupLogFileName="$myBackupFolder/"backup_log_"$(date +'%Y_%m')".txt
DoBackup()
{
myDatabaseName=$1
myCurrentDateTime="$(date +'%d_%m_%Y_%H_%M_%S')"
myBackupFileName="db_backup_${myDatabaseName}_${myCurrentDateTime}".gz
myFullyQualifieldBackupFileName="$myBackupFolder/$myBackupFileName"
echo "mysqldump of $myDatabaseName started at $(date +'%d-%m-%Y %H:%M:%S')" >> "$myBackupLogFileName"
mysqldump --user=root --password=xxxx --default-character-set=utf8 --single-transaction $myDatabaseName | gzip > "$myFullyQualifieldBackupFileName"
echo "mysqldump of $myDatabaseName finished at $(date +'%d-%m-%Y %H:%M:%S')" >> "$myBackupLogFileName"
chown iwiseman "$myFullyQualifieldBackupFileName"
chown iwiseman "$myBackupLogFileName"
echo "file permission changed" >> "$myBackupLogFileName"
find "$myBackupFolder" -name db_backup_* -mtime +8 -exec rm {} \;
echo "old files deleted" >> "$myBackupLogFileName"
echo "operation finished at $(date +'%d-%m-%Y %H:%M:%S')" >> "$myBackupLogFileName"
echo "*****************" >> "$myBackupLogFileName"
}
DoBackup mail
DoBackup wordpress424
exit 0
Fix Playstation
Fix Playstation (Linux)
The works when enp1s0 is the interface of the second NIC and enp2s0 is the main NIC.
To fix the playstation create the following script
#!/bin/bash
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables -A FORWARD -i enp1s0 -o enp2s0 -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i enp2s0 -o enp1s0 -j ACCEPT
Put this into /etc/rc.local e.g
#!/bin/bash
/usr/local/bin/fix_playstation.sh
Fix Playstation (Windows)
Setting network up for two nics with windows you use ICS and then let the playstation connect automatically
Setting up L2TP VPN
You will need the following
Connection Name: xxxxxx Username: xxxxxxx Password: xxxxxxx ServerAddress: xxxxxxx VPN Type: L2TP/IPsec with pre-shared key Pre-shared key: xxxxxx Under IPSec Settings (Linux) 3des-sha1-modp1024 for phase 1 (Linux) 3des-sha1 for phase 2 (Linux) Authentication Methods: Pap, MSChapV2, Chap (Windows only) EncryptionLevel: Optional (Windows only)
sudo apt-get install network-manager-l2tp
sudo apt-get install network-manager-l2tp-gnome
sudo service xl2tpd stop
sudo update-rc.d xl2tpd disable
Install Jenkins
This was done on a 20.04 Ubuntu server
We need java. On the page it says it supports OpenJDK JDK / JRE 8 - 64 bits and OpenJDK JDK / JRE 11 - 64 bits so we need to make sure it uses the right one by creating a .profile.(Note bashrc does not run for this user)
Install java
apt install openjdk-11-jdk-headless
Change the default to 11
sudo update-alternatives --config java
Install Jenkins
wget -q -O - https://pkg.jenkins.io/debian-stable/jenkins.io.key | sudo apt-key add -
sudo sh -c 'echo deb https://pkg.jenkins.io/debian-stable binary/ > \
/etc/apt/sources.list.d/jenkins.list'
sudo apt-get update
sudo apt-get install jenkins
Create a startup script
cat /var/lib/jenkins/.profile
export JAVA_HOME=/usr/lib/jvm/java-11-openjdk-amd64
echo $JAVA_HOME
export PATH=$JAVA_HOME/bin:$PATH
Change the startup script etc init.d/jenkins
PATH=
....
export JAVA_HOME=/usr/lib/jvm/java-11-openjdk-amd64
echo $JAVA_HOME
export PATH=$JAVA_HOME/bin:$PATH
Change the java back
sudo update-alternatives --config java
Open LDAP
Install software
sudo apt install slapd ldap-utils
Reconfigure to your Domain
sudo dpkg-reconfigure slapd
You can verify this has worked with (don't forget sudo)
sudo ldapsearch -x -LLL -b "" -s base namingContexts
It should return your setup in my case
dn: namingContexts: dc=bibble,dc=co,dc=nz
And view the RootDN
sudo ldapsearch -H ldapi:/// -Y EXTERNAL -b "cn=config" -LLL -Q | grep olcRootDN:
It should return
p olcRootDN: olcRootDN: cn=admin,cn=config olcRootDN: cn=admin,dc=bibble,dc=co,dc=nz
Configuring Logging
To view the log level
sudo ldapsearch -H ldapi:/// -Y EXTERNAL -b "cn=config" -LLL -Q | grep olcLogLevel:
Which returns
p olcLogLevel: olcLogLevel: none
We can either use
sudo ldapmodify -Y EXTERNAL -H ldapi:/// -Q
To modify interactively or use LDIF files to update. Either way the contents are
dn: cn=config changeType: modify replace: olcLogLevel olcLogLevel: stats
To perform using LDIF use
sudo ldapmodify -Y EXTERNAL -H ldapi:/// -f /tmp/test.ldif
And verify with
sudo ldapsearch -Y EXTERNAL -H ldapi:/// -b cn=config "(objectClass=olcGlobal)" olcLogLevel -LLL -Q
Setting up log files
Lets put the logs into their own file
sudo vi /etc/rsyslog.d/51-slapd.conf
Add the following
local4.* /var/log/slapd.log
Restart
sudo systemctl restart rsyslog slapd
Lets clean up the logs
sudo vi /etc/logrotate.d/slapd
Add the following
/var/log/slapd.log
{
rotate 7
daily
missingok
notifempty
delaycompress
compress
postrotate
/usr/lib/rsyslog/rsyslog-rotate
endscript
}Restart
sudo systemctl restart logrotate
Set up ssl
The are three certs to worry about
rootCA server cert server key
I create these independently of this setup and these are place in
/etc/ssl/openldap/certs/rootCA.pem /etc/ssl/openldap/certs/server.crt /etc/ssl/openldap/private/server.key
Set permissions on the directory
chown -R openldap: /etc/ssl/openldap/
We need to allow apparmor to read the files so edit
vi /etc/apparmor.d/usr.sbin.slapdWith
...
# Site-specific additions and overrides. See local/README for details.
#include
#TLS
/etc/ssl/openldap/certs/ r,
/etc/ssl/openldap/certs/* r,
/etc/ssl/openldap/private/ r,
/etc/ssl/openldap/pri /etc/letsencrypt/archive/ldap.bibble.co.nz/ r,
/etc/letsencrypt/archive/ldap.bibble.co.nz/* r,vate/* r,Reload
apparmor_parser -r /etc/apparmor.d/usr.sbin.slapdCreate a ldif to reflect your cert names and locations
dn: cn=config
changetype: modify
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/ssl/openldap/certs/cacert.pem
-
replace: olcTLSCertificateFile
olcTLSCertificateFile: /etc/ssl/openldap/certs/ldapserver-cert.crt
-
replace: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/ssl/openldap/private/ldapserver-key.keyHad a lot of trouble getting the next bit to work thanks to no help from the product. Firstly add the ssl-cert to the openldap with
usermod -aG ssl-cert openldapAlso found that the key was read only for letsencryt so
chmod g+r /etc/letsencrypt/archive/DOMAIN/privkey1.pemThe trick is to get the permissions right. I did this by looking at what others had done. Namely /etc/ssl. I checked the permisions on directories cert and private plus the contents and owner. Here is the end result
root@oliver:/etc/ssl# ls -lR openldap/
openldap/:
total 8
drwxr-xr-x 2 openldap openldap 4096 Nov 4 13:39 certs
d-wx--x--- 2 openldap ssl-cert 4096 Nov 4 13:39 private
openldap/certs:
total 8
-rw-r--r-- 1 openldap ssl-cert 1411 Nov 4 13:39 rootCA.pem
-rw-r--r-- 1 openldap ssl-cert 1501 Nov 4 13:39 server.crt
openldap/private:
total 4
-rw-r----- 1 openldap ssl-cert 1704 Nov 4 13:39 server.keyNow you should be able to add then TLS entries with
ldapmodify -Y EXTERNAL -H ldapi:/// -f ldap-tls.ldifAs ever you can verify this with
slapcat -b "cn=config" | grep -E "olcTLS"Which should show
olcTLSCACertificateFile: /etc/ssl/openldap/certs/rootCA.pem
olcTLSCertificateKeyFile: /etc/ssl/openldap/private/server.key
olcTLSCertificateFile: /etc/ssl/openldap/certs/server.crtLet run a test before switching
slaptest -uWhich should show
config file testing succeededAdd the certificate int /etc/ldap/ldap.conf
...
# TLS certificates (needed for GnuTLS)
#TLS_CACERT /etc/ssl/certs/ca-certificates.crt
TLS_CACERT /etc/ssl/openldap/certs/rootCA.pemRestart the server
systemctl restart slapdFinally, phew test the connectivity
ldapwhoami -H ldapi:/// -x -ZZFor lets encrypt I ended up with
ls -lR /etc/ssl/openldap/
/etc/ssl/openldap/:
total 8
drwxr-xr-x 2 openldap openldap 4096 Nov 4 05:30 certs
drwxr-xr-x 2 openldap ssl-cert 4096 Nov 4 05:31 private
/etc/ssl/openldap/certs:
total 0
lrwxrwxrwx 1 openldap openldap 53 Nov 4 05:30 rootCA.pem -> /etc/letsencrypt/live/XXX/fullchain.pem
lrwxrwxrwx 1 openldap openldap 48 Nov 4 05:30 server.crt -> /etc/letsencrypt/live/XXX/cert.pem
/etc/ssl/openldap/private:
total 0
lrwxrwxrwx 1 openldap ssl-cert 51 Nov 4 05:31 server.key -> /etc/letsencrypt/live/XXX/privkey.pemAnd the ldif
dn: cn=config
changetype: modify
add: olcTLSCipherSuite
olcTLSCipherSuite: NORMAL
-
add: olcTLSCRLCheck
olcTLSCRLCheck: none
-
add: olcTLSVerifyClient
olcTLSVerifyClient: never
-
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/ssl/openldap/certs/rootCA.pem
-
add: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/ssl/openldap/private/server.key
-
add: olcTLSCertificateFile
olcTLSCertificateFile: /etc/ssl/openldap/certs/server.crt
-
add: olcTLSProtocolMin
olcTLSProtocolMin: 3.3You can test this with
sudo ldapwhoami -H ldap://ldap.bibble.co.nz -x -ZZ
Add a user
Create a base dn
dn: ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: organizationalUnit
ou: people
dn: ou=group,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: organizationalUnit
ou: groupAnd add a user as below creating first a password with slappasswd
dn: uid=mibeyam,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: mibeyam
cn: mibeyam
givenName: Amos
sn: Mibey
userPassword: {SSHA}sO8V/PZsGCta6098vs2qgX767AJF3Sw7
loginShell: /bin/bash
uidNumber: 10000
gidNumber: 10000
homeDirectory: /home/mibeyam
dn: cn=mibeyam,ou=group,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: posixGroup
cn: mibeyam
gidNumber: 10000
memberUid: mibeyamSet up client
You will need to know your base DN which is the first line of slapcat
I would recommend you test you user on the client prior to provisioning using you DN and account
ldapwhoami -vvv -h localhost -D "uid=mibeyam,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com" -x -W
A good result will echo the user
Install software
sudo apt-get update
sudo apt-get install libpam-ldapd libnss-ldapd
Change pam to create directory /etc/pam.d/common-session
...
session required pam_mkhomedir.so umask=0022 skel=/etc/skelRestart services sudo systemctl restart nslcd sudo systemctl restart nscd
Screen Blanking
After suspend the screen kept blanking after 33 seconds. To fix this we need to do
# Query
xset q
# Turn off dpms
xset -dpms
Set up 5.1
For current setup (ALC1220-VB) I used this. The Orange, Black and Green
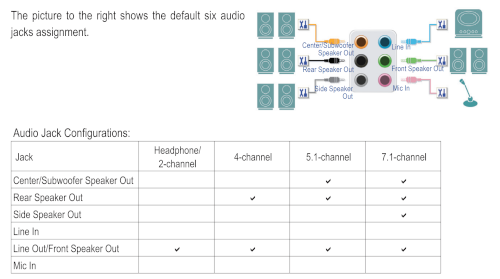
Here is the Z506 relevant page
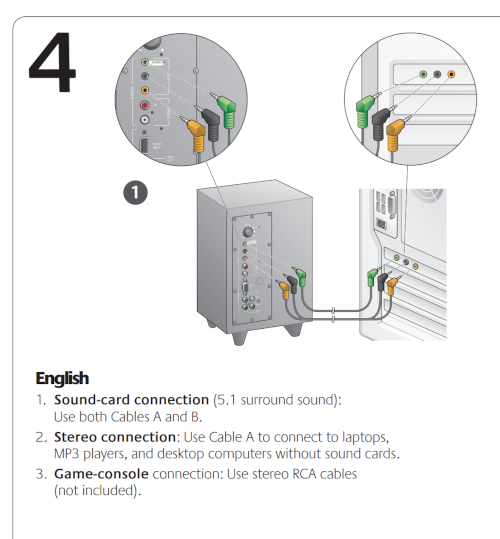
Maybe an order to this. But set the channels to 6 after selecting the card
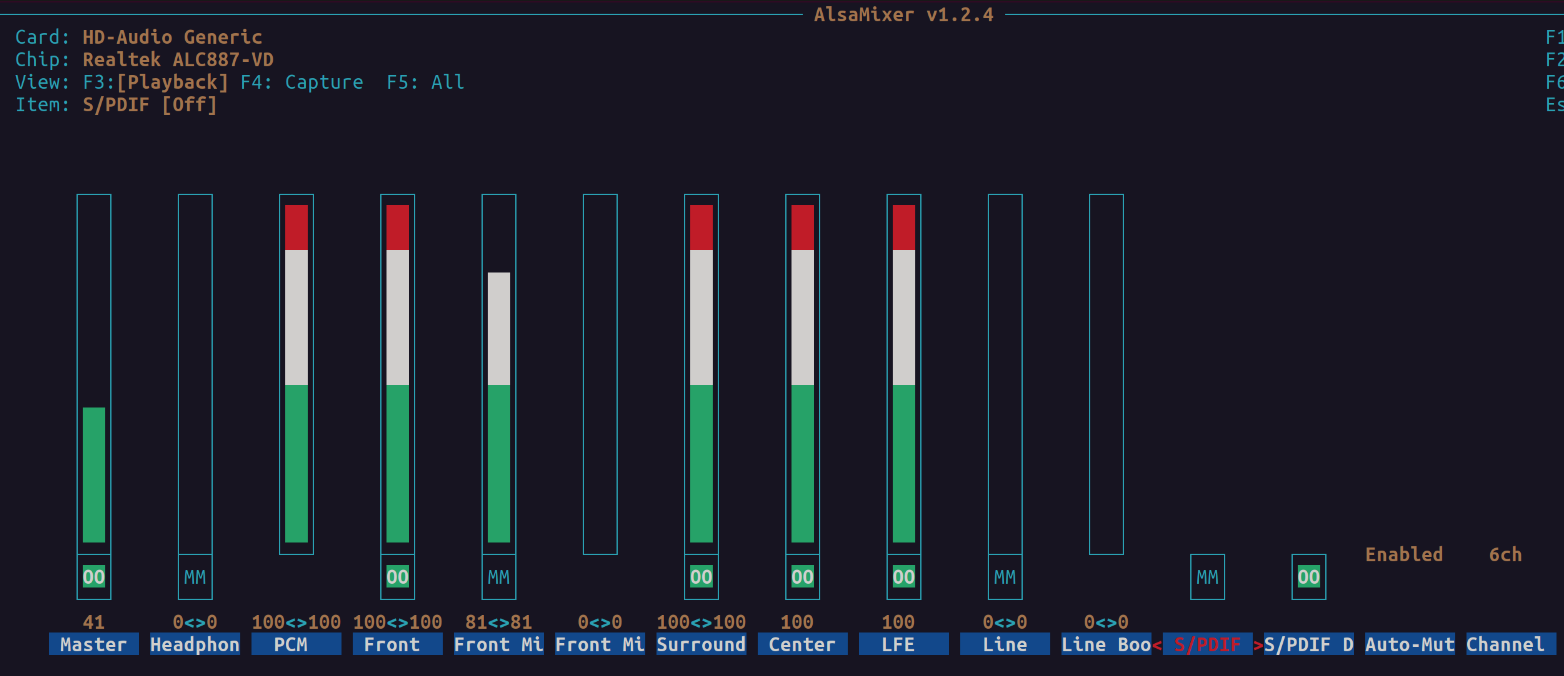
Change /etc/pulse/daemon.conf to have the correct channels and mapping. The mapping may be different for different systems.
default-sample-channels = 6
default-channel-map = front-left,front-right,rear-left,rear-right,front-center,lfeAnd here is a picture taken by my wifey

Sound starting produces two Crackles
When sound starts you hear two crackle and then sound works. This is caused by power saving and you can turn this off with the following
echo "0" | sudo tee /sys/module/snd_hda_intel/parameters/power_save
If this works we can make this permanent
echo "options snd_hda_intel power_save=0" | sudo tee -a /etc/modprobe.d/audio_disable_powersave.conf
PipeWire Alternative to Pulse
Got this from here
Setup
When I did this I had to reboot but then it worked
sudo add-apt-repository ppa:pipewire-debian/pipewire-upstream
sudo apt update
sudo apt install pipewire pipewire-audio-client-libraries
sudo apt install gstreamer1.0-pipewire libpipewire-0.3-{0,dev,modules} lib spa-0.2-{bluetooth,dev,jack,modules} pipewire{,-{audio-client-libraries,pulse,media-session,bin,locales,tests}}
sudo systemctl --user daemon-reload
// Disable pulse
systemctl --user --now disable pulseaudio.service pulseaudio.socket
// Enable pipewire
systemctl --user --now enable pipewire pipewire-pulse
Pactl info
Remove
Not run this because the above did work
sudo apt remove pipewire pipewire-audio-client-libraries
sudo apt remove gstreamer1.0-pipewire libpipewire-0.3-{0,dev,modules} libspa-0.2-{bluetooth,dev,jack,modules} pipewire{,-{audio-client-libraries,pulse,media-session,bin,locales,tests}}
systemctl --user daemon-reload
systemctl --user --now enable pulseaudio.service pulseaudio.socket
pactl info
Set up Fake Cam
Download Fake Cam Linux-Fake-Background-Webcam
git clone https://github.com/fangfufu/Linux-Fake-Background-Webcam
Set up a modprobe for it in /etc/modprobe.d/fakecam.conf
options v4l2loopback devices=1 video_nr=20 card_label=fakecam exclusive_caps=1Force module to be loaded at boot by adding v4l2loopback to /etc/modules
Now add a script for convenience e.g. ~/bin/cam.sh
#!/usr/bin/bash
cd ~/dev/projects/Linux-Fake-Background-Webcam/
python3 fake.py -v /dev/video20 --no-background --no-foreground
Useful LDAP Commands
List users
ldapsearch -x -LLL -b "dc=ldapmaster,dc=kifarunix-demo,dc=com"
Delete user
ldapdelete -x -W -D "cn=admin,dc=ldapmaster,dc=kifarunix-demo,dc=com" "uid=mibeyam,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com"
Reset password
ldappasswd -H ldapi:/// -x -D "cn=admin,dc=ldapmaster,dc=kifarunix-demo,dc=com" -W -S "uid=mibeyam,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com"
Flush DNS
# Check a Record
nslookup -type=A xxxx.ihc.org.nz
# Restart bind
sudo systemctl restart bind9
# Flush DNS
sudo rndc flush
sudo resolvectl flush-caches
Fix DNS
With the standard approach of using netplan the DNS gets overwritten.
network:
version: 2
renderer: networkd
ethernets:
enp5s0:
addresses: [10.10.1.100/24] # IP Address
gateway4: 10.10.1.1 # Router name
nameservers:
search: [mydomain.local] # Local domain
addresses: [10.10.1.254] # DNS Server
dhcp4: yes
You can fix this with
sudo netplan applyTo fix this need to change /etc/systemd/resolved.conf
...
#Set your DNS and add alternatives
DNS=10.1.1.254 8.8.8.8 9.9.9.9
#Add for local domain
domains=mydomain.local
...To test this you can use
resolvectl
Global
Protocols: -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported
resolv.conf mode: stub
Current DNS Server: 10.10.1.254
DNS Servers: 10.10.1.254 8.8.8.8 9.9.9.9
Link 2 (enp5s0)
Current Scopes: DNS
Protocols: +DefaultRoute +LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported
Current DNS Server: 10.10.1.254
DNS Servers: 10.10.1.254 8.8.8.8 8.8.4.4
DNS Domain: mydomain.localRedirect syslog entries for Process
To redirect the logs for a process create a config with less than 50-default.conf e.g. 30-dhcpd.conf
###############
#### RULES ####
###############
#
# First some standard log files. Log by facility.
#
if $programname == 'dhcpd' then /var/log/dhcp.log
& stopThen make sure you add rotate entry in /etc/logrotate.d/rsyslog
/var/log/syslog
/var/log/mail.info
/var/log/mail.warn
/var/log/mail.err
/var/log/mail.log
/var/log/daemon.log
/var/log/kern.log
/var/log/auth.log
/var/log/user.log
/var/log/lpr.log
/var/log/cron.log
/var/log/debug
/var/log/dhcp.log
/var/log/messages
{
rotate 4
weekly
missingok
notifempty
compress
delaycompress
sharedscripts
postrotate
/usr/lib/rsyslog/rsyslog-rotate
endscript
}
Drag and Drop Broken
This was logged in 23.04 and raised https://bugs.launchpad.net/ubuntu/+source/gnome-shell/+bug/2016743
Workaround is to switch to wayland. https://beebom.com/how-switch-between-wayland-xorg-ubuntu/
MediaWiki URLs
Changed this on the 24 May 2023. Kept the original nginx config but added
# Handling for the article path (pretty URLs)
location /wiki/ {
rewrite ^/wiki/(?<pagename>.*)$ /mediawiki/index.php;
}
We needed to change the LocalSettings.php to
$wgScriptPath = "/mediawiki";
$wgArticlePath = "/wiki/$1";
$wgUsePathInfo = true;To reverse we need to remove both of these.
MS Teams
Cannot get the Progressive App to work so downloaded from
sudo apt install libgdk-pixbuf2.0-0 libgdk-pixbuf-xlib-2.0-0
wget http://repo.linuxliteos.com/linuxlite/pool/main/t/teams/teams_1.5.00.23861_amd64.deb
sudo dpkg -i teams_1.5.00.23861_amd64.deb
Setup WIFI Dongle
This is for the following device
0bda:c820 Realtek Semiconductor Corp. 802.11ac NIC
We have to blacklist the default driver. Create file /etc/modprobe.d/rtw8821bu.conf
blacklist rtw88_8821cu
Add the repository and install driver 5.12.0.4~lunar
sudo add-apt-repository ppa:kelebek333/kablosuz
sudo apt update
sudo apt install rtl8821cu-next-dkms
Fix Bluetooth BORIS
Remove the device Turn bluetooth off
bluetoothctl
And type
[bluetooth]# agent off
[bluetooth]# power off
[bluetooth]# power on
[bluetooth]# agent on
[bluetooth]# default-agent
[bluetooth]# scan onFix Router in Living Room
Symptoms were
- Orange on living room LAN (Green when working)
Windows 10 USB Boot on linux
Use [Ventoy] software. When you burn the USB it takes forever to umount. To monitor write blocks on USB use
watch grep -e Dirty: -e Writeback: /proc/meminfo
Fix PulseWire with MS Teams
systemctl --user restart pipewire.socket
systemctl --user --now enable pipewire
Set up Azure Text-To-Speech
Here are the steps I needed to step up speech for Visual Studio
Set up Azure
For this you need an account and to create a speech Resource
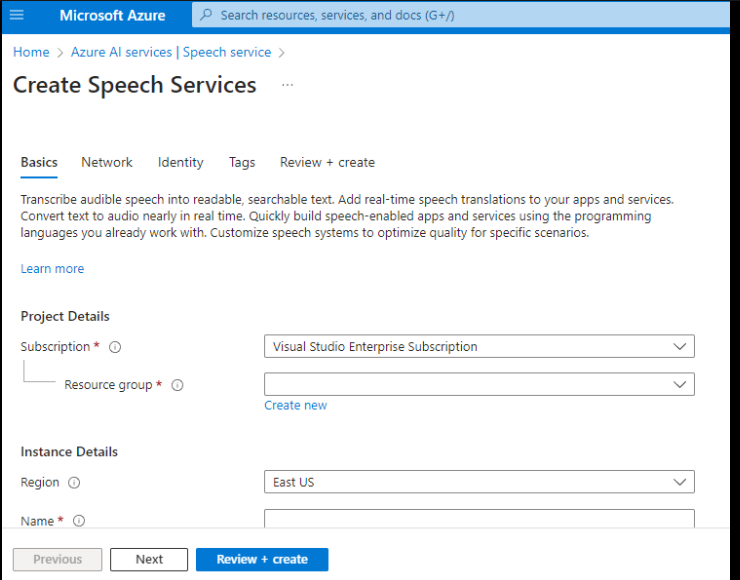
From there you need to create a key and note down the region you are using
Fix it being Broken
It does not work out of the box you need to do two things
- Set SSL_CERT_FILE=/etc/ssl/certs/ca-certificates.crt
Next you need to make sure your default mic is correct to do this first list your available mics with the command
arecord -l
Create a ~/.asoundrc file and put the add the following. In my case my mic was card 3
defaults.pcm.card 3
defaults.ctl.card 3Finishing up
Make sure you have
- SPEECH_KEY=xxxxx and
- SPEECH_REGION=australiaeast
- SSL_CERT_FILE=/etc/ssl/certs/ca-certificates.crt
as environment variables in your profile. I put mine in .bashrc
Set up OBS and Virtual Cam
First install OBS from package manager. Then install v4l2loopback-dkms
sudo apt install v4l2loopback-dkms
No virtual camera will appear unless you modprobe this
sudo modprobe v4l2loopback-dkms
To automate this we can automate this
With /etc/modprobe.d/v4l2loopback.conf
options v4l2loopback video_nr=99 card_label="OBS Video Source" exclusive_caps=1
And /etc/modules-load.d/v4l2loopback.conf
v4l2loopback