Setting up localhost SSL Cert: Difference between revisions
Jump to navigation
Jump to search
Created page with "Create a file server.csr.cnf <syntaxhighlight code=""> openssl genrsa [req] default_bits = 2048 prompt = no default_md = sha256 distinguished_name = dn [dn] C=US ST=RandomSta..." |
No edit summary |
||
| (8 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
Create a file server.csr.cnf | =Create a file server.csr.cnf= | ||
<syntaxhighlight code=""> | <syntaxhighlight code=""> | ||
openssl genrsa | openssl = genrsa | ||
[req] | [req] | ||
default_bits = 2048 | default_bits = 2048 | ||
| Line 17: | Line 17: | ||
CN = localhost | CN = localhost | ||
</syntaxhighlight> | </syntaxhighlight> | ||
<br> | |||
Create a file v3.ext | =Create a file v3.ext= | ||
<syntaxhighlight code=""> | <syntaxhighlight code=""> | ||
authorityKeyIdentifier=keyid,issuer | authorityKeyIdentifier=keyid,issuer | ||
| Line 27: | Line 28: | ||
[alt_names] | [alt_names] | ||
DNS.1 = localhost | DNS.1 = localhost | ||
IP.1 = 192.168.1.70 | |||
</syntaxhighlight> | </syntaxhighlight> | ||
<br> | |||
=run the following= | |||
<syntaxhighlight code="bash"> | <syntaxhighlight code="bash"> | ||
openssl genrsa -des3 -out rootCA.key 2048 | openssl genrsa -des3 -out rootCA.key 2048 | ||
| Line 34: | Line 39: | ||
openssl req -new -sha256 -nodes -out server.csr -newkey rsa:2048 -keyout server.key -config <( cat server.csr.cnf ) | openssl req -new -sha256 -nodes -out server.csr -newkey rsa:2048 -keyout server.key -config <( cat server.csr.cnf ) | ||
openssl x509 -req -in server.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out server.crt -days 500 -sha256 -extfile v3.ext | openssl x509 -req -in server.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out server.crt -days 500 -sha256 -extfile v3.ext | ||
</syntaxhighlight> | |||
=Angular= | |||
Just add the certs in | |||
<syntaxhighlight code="json"> | |||
"serve": { | |||
"builder": "@angular-devkit/build-angular:dev-server", | |||
"options": { | |||
"browserTarget": "bibbleWeb:build", | |||
"ssl": true, | |||
"sslKey": "../not_saying_relative_to_project/server.key", | |||
"sslCert": "../not_saying_relative_to_project/server.crt" | |||
}, | |||
</syntaxhighlight> | |||
=And import it in Chrome= | |||
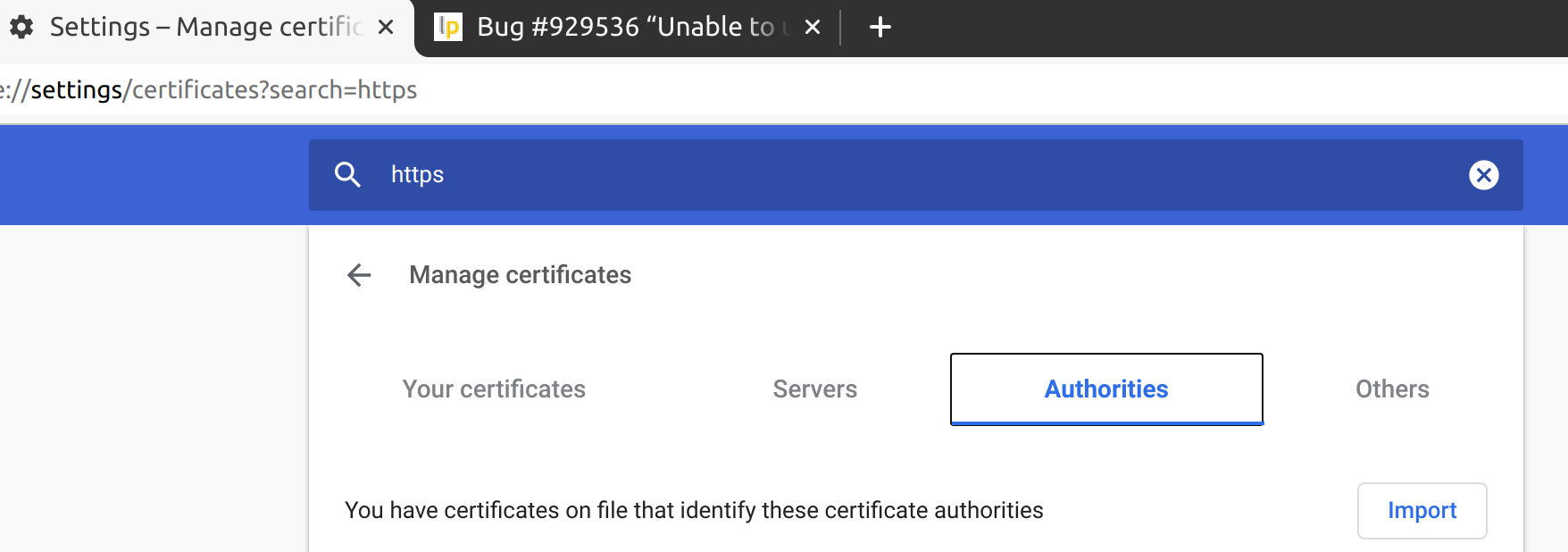
Import the rootCA.pem into chrome under the authorities page<br> | |||
[[File:Chrome cert import.png|800px]] | |||
=Convert to a .P12= | |||
We can convert this to a .p12 with the following command | |||
<syntaxhighlight lang="bash"> | |||
openssl pkcs12 -export -out server.p12 -inkey server.key -in server.crt -certfile rootCA.pem | |||
</syntaxhighlight> | |||
=Add Certificates to Ubuntu= | |||
For my local network you need to add the certificates to the server. This is what I do. | |||
<syntaxhighlight lang="bash"> | |||
cp server.crt /etc/ssl/certs/<IP>-server.crt | |||
cp server.key /etc/ssl/private/<IP>-server.key | |||
sudo update-ca-certificates | |||
</syntaxhighlight> | </syntaxhighlight> | ||
Latest revision as of 03:22, 10 April 2025
Create a file server.csr.cnf
openssl = genrsa
[req]
default_bits = 2048
prompt = no
default_md = sha256
distinguished_name = dn
[dn]
C=US
ST=RandomState
L=RandomCity
O=RandomOrganization
OU=RandomOrganizationUnit
emailAddress=hello@example.com
CN = localhost
Create a file v3.ext
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = localhost
IP.1 = 192.168.1.70
run the following
openssl genrsa -des3 -out rootCA.key 2048
openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 1024 -out rootCA.pem
openssl req -new -sha256 -nodes -out server.csr -newkey rsa:2048 -keyout server.key -config <( cat server.csr.cnf )
openssl x509 -req -in server.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out server.crt -days 500 -sha256 -extfile v3.extAngular
Just add the certs in
"serve": {
"builder": "@angular-devkit/build-angular:dev-server",
"options": {
"browserTarget": "bibbleWeb:build",
"ssl": true,
"sslKey": "../not_saying_relative_to_project/server.key",
"sslCert": "../not_saying_relative_to_project/server.crt"
},And import it in Chrome
Import the rootCA.pem into chrome under the authorities page
Convert to a .P12
We can convert this to a .p12 with the following command
openssl pkcs12 -export -out server.p12 -inkey server.key -in server.crt -certfile rootCA.pem
Add Certificates to Ubuntu
For my local network you need to add the certificates to the server. This is what I do.
cp server.crt /etc/ssl/certs/<IP>-server.crt
cp server.key /etc/ssl/private/<IP>-server.key
sudo update-ca-certificates