OAuth 2.0: Difference between revisions
| Line 54: | Line 54: | ||
[[File:Authorization Code Flow.png|600px]]<br> | [[File:Authorization Code Flow.png|600px]]<br> | ||
===Step 1 - Authorization Request=== | ====Step 1 - Authorization Request==== | ||
To make an Authorization request we send | To make an Authorization request we send | ||
*Response Type | *Response Type | ||
| Line 61: | Line 61: | ||
*state (optional) | *state (optional) | ||
*scope parameters (optional) | *scope parameters (optional) | ||
===Step 2 - Authorization Response=== | ====Step 2 - Authorization Response==== | ||
This redirect to the Url in the request and returns | This redirect to the Url in the request and returns | ||
*code | *code | ||
*state (optionally) | *state (optionally) | ||
===Step 3 - POST Token Request=== | ====Step 3 - POST Token Request==== | ||
The parameters include | The parameters include | ||
*Host (e.g. myserver.co.nz) | *Host (e.g. myserver.co.nz) | ||
| Line 78: | Line 78: | ||
*RFC 7617 Base64(client_id + ":" + client_secret) | *RFC 7617 Base64(client_id + ":" + client_secret) | ||
*RFC 67649 Base64(urlformencode(client_id) + ":" + urlformencode(client_secret)) | *RFC 67649 Base64(urlformencode(client_id) + ":" + urlformencode(client_secret)) | ||
====Step 4 - Token Request Response==== | |||
===Step 4 - Token Request Response=== | |||
If successful we will get | If successful we will get | ||
*access_token | *access_token | ||
| Line 85: | Line 84: | ||
*expiry (in seconds) | *expiry (in seconds) | ||
*scope (optional) | *scope (optional) | ||
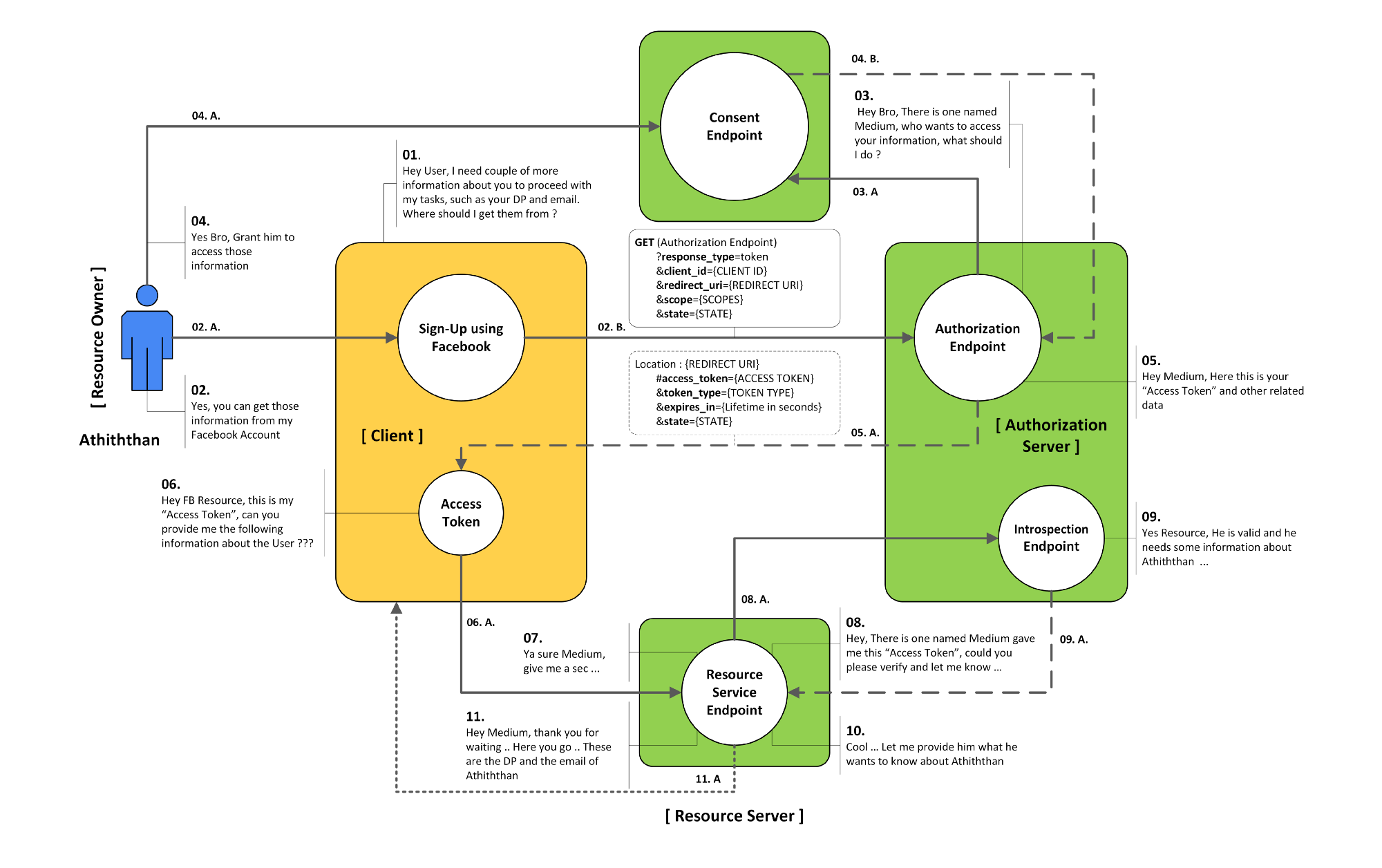
==Implicit Grant Type Flow== | ==Implicit Grant Type Flow== | ||
The Implicit Grant Type is intended to be used by user-agent based clients (Example: SPA), which can’t keep a client secret because all of the application code and storage is easily accessible. | The Implicit Grant Type is intended to be used by user-agent based clients (Example: SPA), which can’t keep a client secret because all of the application code and storage is easily accessible. | ||
[[File:Implicit Flow.png|500px]]<br> | [[File:Implicit Flow.png|500px]]<br> | ||
Revision as of 11:43, 18 July 2021
Introduction
History
Previously we used
- XML
- SOAP
- SAML or WS-*
Now we Use
- JSON
- HTTP APIs
- OAuth and OpenID Connect
Credential Sharing
Previously we used to use credential Sharing. E.g. Problems with this are
- We can impersonate the use
- Issues around revocation
- Exposed user credentials
Cookies
Next solution was cookies but CSRF and XSRF attacks were common.
API Key
Next API Key, this works well accept for where the app has no backend. E.g. Single Page App.
- API Keys have no standard
- Expiration management
OAuth 2.0
Features include
- Authorization framework
- Built for HTTP APIs
- Scoped access (User defined what can be used)
- Delegation Protocol
Players include
- Protected Resource (Our API)
- Client (requesting application)
- Resource Owner (the user)
- Authorization Server
Here is the flow for OAuth 2.0
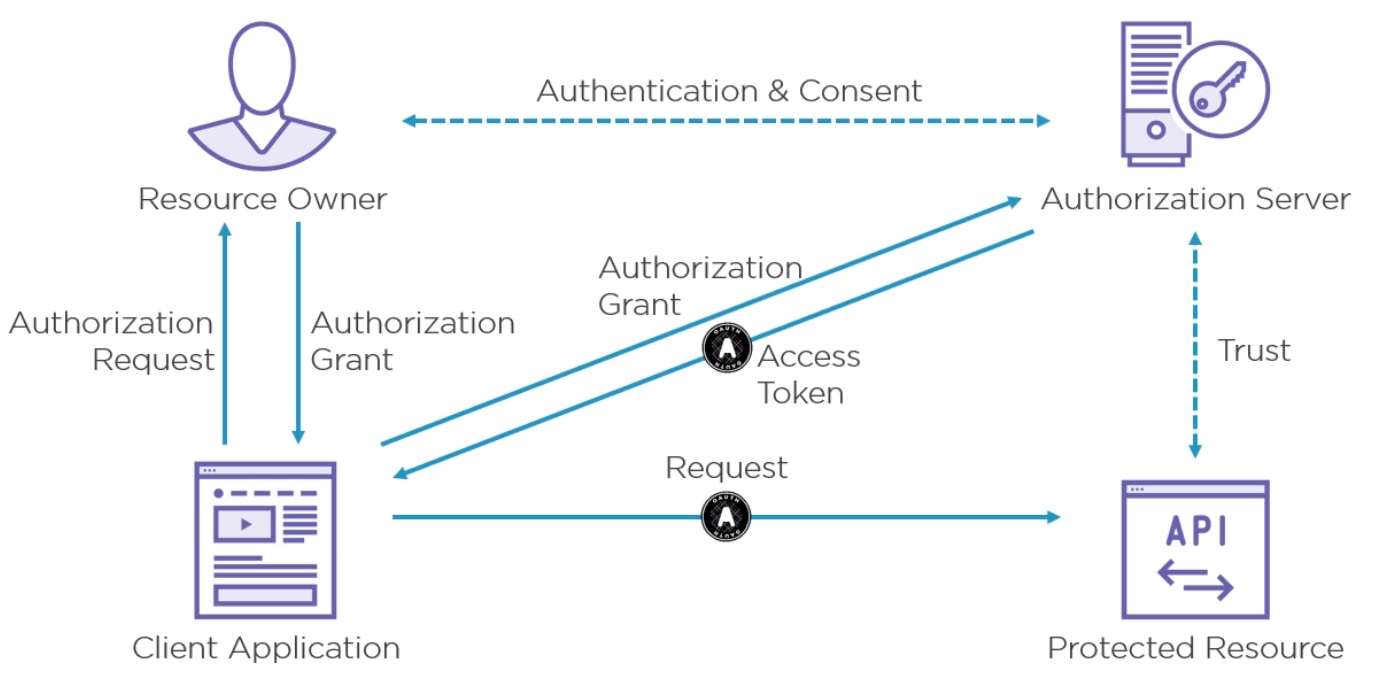
How the API trusts the access token is out of scope for OAuth but if is up to the Protected Resource to do this before sending the response.
Detail
Endpoints
The Protocol endpoint are either
- Authorization Handles all user interaction by the user agent
- Token - This endpoint is for machines only
Scope
A scope in OAuth is a permission to do something with a protected resource. E.g. access to API, Read/Write, Feature.
Grant Types
Types
There are five Grant Types
- Authorization Code Grant Type ()
- Implicit Grant Type
- Resource Owner Credentials Grant Type
- Client Credentials Grant Type
- Refresh Token Grant
Authorization Code Grant Type Flow
The Authorization Code Grant Type is the most commonly used grant type to authorize the Client to access protected data from a Resource Server.
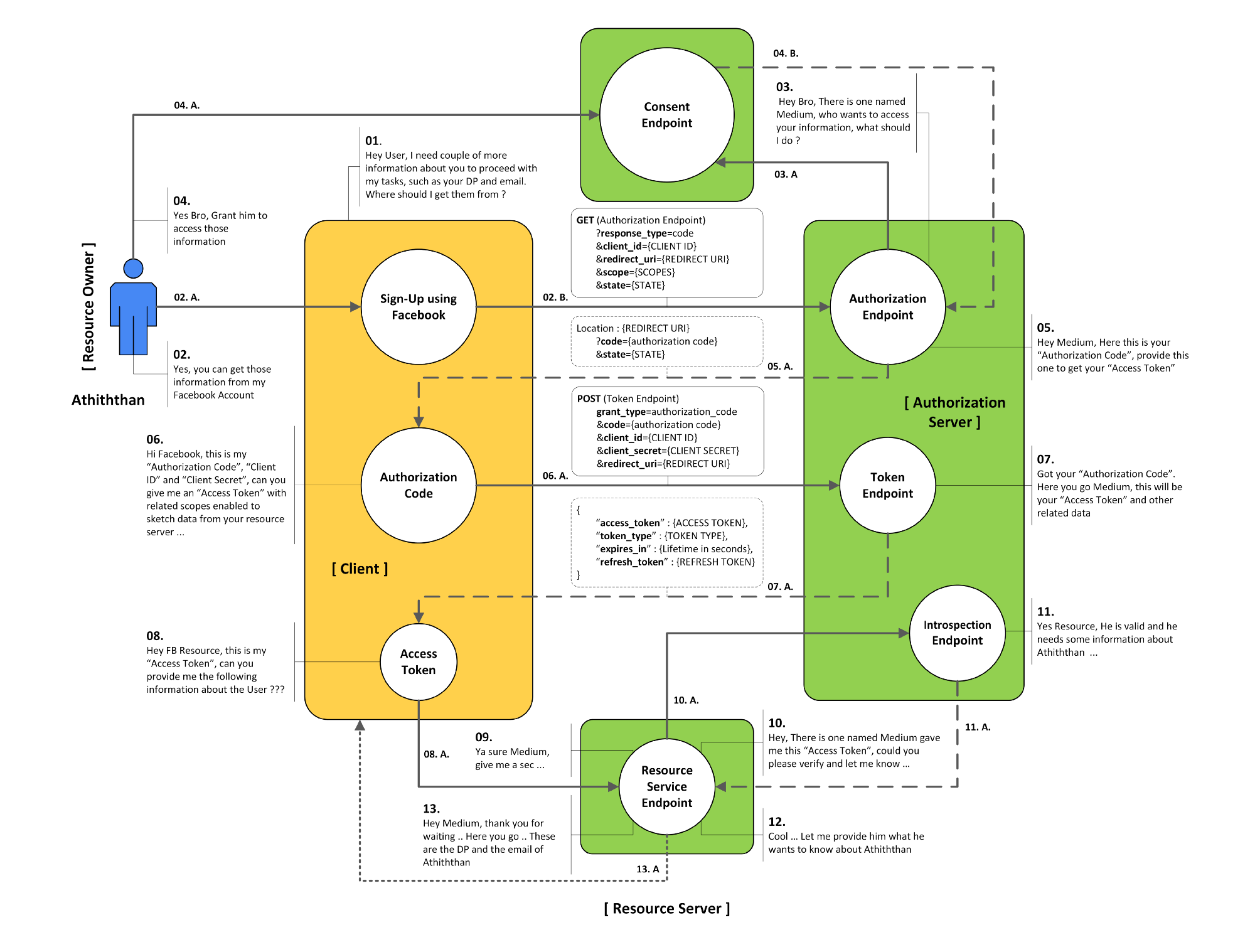
Step 1 - Authorization Request
To make an Authorization request we send
- Response Type
- Client Id
- Redirect Uri
- state (optional)
- scope parameters (optional)
Step 2 - Authorization Response
This redirect to the Url in the request and returns
- code
- state (optionally)
Step 3 - POST Token Request
The parameters include
- Host (e.g. myserver.co.nz)
- Content Type (e.g. x-www-for-urlencoded)
- Authorization (e.g. Basic)
The POST body must include a body with
- grant_type=authorization_code
- code=authorization_code (from step 2)
- redirect_uri=https://client.example.cb
There are two forms of Basic Authentication
- RFC 7617 Base64(client_id + ":" + client_secret)
- RFC 67649 Base64(urlformencode(client_id) + ":" + urlformencode(client_secret))
Step 4 - Token Request Response
If successful we will get
- access_token
- token_type
- expiry (in seconds)
- scope (optional)
Implicit Grant Type Flow
The Implicit Grant Type is intended to be used by user-agent based clients (Example: SPA), which can’t keep a client secret because all of the application code and storage is easily accessible.